In the ever-evolving landscape of cybersecurity, discussions have witnessed a transformation. Initially, the primary focus revolved around securing client data to prevent financial and reputational risks. This led to substantial investments in fortifications like Single Sign-On (SSO), Multi-Factor Authentication (MFA), and a shift towards cloud-based software with robust online security measures. As data protection improved, cybercriminals adapted, shifting their attention towards exploiting vulnerabilities within the very core of communication – Email.
Email: The Gateway for Cybercriminals
Imagine this: having control over someone's email account is akin to holding their digital identity hostage. Essentially, email serves as the key that unlocks access to relationships, applications, and critical data – the holy grail for hackers.
Here are 3 trends that underline why email stands as the primary cyber threat for accountants in 2023:
-
1. Surge in Email Activity Post-Pandemic
The COVID-19 pandemic triggered an unprecedented surge in email activity among accountants. This mirrors the changing landscape of business communication and collaboration. Practice management tools such as Karbon swiftly adapted by introducing features like a triage center, which efficiently converts emails into actionable tasks. With email emerging as the front line for rapid decision-making and client interactions, hackers are seizing the opportunity. The sheer volume of emails has made it increasingly difficult for time-pressed accountants to differentiate legitimate messages from potential threats, enabling well-crafted phishing emails to seamlessly blend in.
-
2. Targeted Phishing Takes the Spotlight
Email compromise techniques have evolved into more sophisticated forms. Hackers have moved beyond the spray-and-pray approach, now employing precise, targeted phishing tactics. Their focus often lies on industries that house sensitive information and trusted payment partners. Spear-phishing attacks are especially prominent within accounting firms, honing in on leadership figures who possess valuable financial data and may lack extensive cybersecurity training. Shockingly, 2022 saw the highest-ever rate of mobile phishing attacks, as highlighted by Lookout.
-
3. AI Enhances Impersonation Attacks
The advent of AI-powered tools has elevated the art of impersonation attacks. A recent study disclosed that a staggering 67% of email-based cyberattacks now leverage AI technology, rendering them considerably more challenging to detect and counter. Tools like ChatGPT have transcended language barriers, enabling hackers from non-English speaking regions to seamlessly replicate communication styles. This surge in highly targeted impersonation attacks has left organizations grappling with unprecedented detection challenges.
Introducing Business Email Compromise (BEC) Attacks
In light of the trends mentioned above, accounting firms entrusted with sensitive client information are confronting a growing surge of email-based cybersecurity challenges often referred to as Business Email Compromise (BEC) attacks. These malicious schemes revolve around identity fraud and employ social engineering tactics to exploit trust, coercing individuals into revealing confidential data or engaging in actions that serve the attacker's interests.
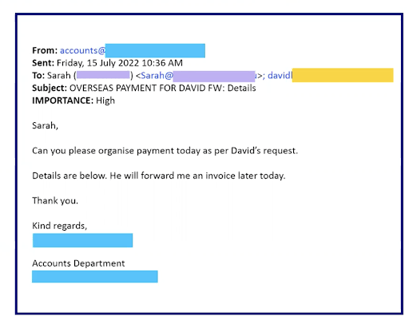
The manifestations of BEC attacks are as varied as the emails that traverse business networks. Here are some typical examples, though it's crucial to recognize that this list isn't exhaustive, given cybercriminals' ongoing ingenuity in concealing their schemes within legitimate email communications:
CEO Fraud: Cybercriminals impersonate high-ranking executives, frequently CEOs or CFOs, to illicitly procure payments or wire transfers.
Vendor Email Compromise: Attackers infiltrate a vendor's email account to dispatch deceptive invoices or payment requests to unsuspecting customers.
Data Breach: Cyber miscreants infiltrate an employee's email account to pilfer sensitive information, which can be exploited in subsequent attacks or sold on the dark web.
Gift Card Scams: Perpetrators mimic executives or suppliers to coerce employees into purchasing gift cards.
Account Takeovers: Hackers seize control of employee email accounts, dispatching fraudulent payment requests or gaining access to sensitive data.
Defending Against BEC Threats
So, what's the defense strategy against BEC threats?
Effectively thwarting BEC attacks hinges on three core pillars: Technology, a well-informed team, and robust policies.
Technology
A strong defense surpasses standard data protection protocols. Prioritize identity and permission safeguards, utilizing industry-specific access management platforms such as Practice Protect. Integrate multi-factor authentication, restrict login by geographical region, proactively monitor suspicious activities, and activate notification systems. Practice Protect's Email Hub reinforces email confidentiality and integrity, bolstering your firm's resilience against phishing, malware, and spam.
Team
It's worth remembering that BEC attacks target individuals, not just systems. Comprehensive education is paramount. Train your team to recognize the signs of BEC attacks, spot fraudulent emails, and respond appropriately. Leverage resources like the Small Business Cyber Security Guide and Practice Protect University's security training for comprehensive insights.
Policy
Establish clear policies governing critical processes. Revise payment policies to mandate telephone confirmations for new account details. Extend analogous procedures to clients, implementing secondary confirmation protocols. Scrutinize insurance policies for coverage against social engineering attacks like BEC. Lastly, institute transparent IT and internet usage policies that are well-understood by all employees.
Guarding against BEC threats requires a collective commitment, ensuring your firm's integrity, preserving client trust, and fortifying your financial security. Act promptly to safeguard your digital realm.
.png?width=150&height=63&name=TWRlogo-regmark_blueblack%20(1).png)
.png)








Do you have questions about this article? Email us and let us know > info@woodard.com
Comments: