Do you really know what it means to have data secured? Do you understand how encryption works? Are all your client files truly secure?
If you’re the least bit nerdy, like me, then strap in! I have some super nerdy stuff coming at ya! Full disclosure: I’m super nerdy. Like computer specs, video games, and how the universe works nerdy. I like knowing things…all the things. But for now, we’re going to discuss security, more specifically, we’re going to talk about what encryption is and why it matters.
Salad time.
Not really, but there is a tie-in here. One of the first forms of encryption was called the Caesar Cipher by none other than Julius Caesar. (Side note: in my former life as a high school English teacher, I taught the play every year. I really don’t miss the groans that accompanied telling my students we’re about to read Shakespeare.) This form of primitive encryption was used to allow Caesar to send military directives to troops in a way that was unreadable if intercepted. Cool, huh? Now back to a more modern era.
Now, when you think of the word encryption, you might think of this secure vault where computer data is stored, but that’s not really what it is. Like, not even a little. At its base, EVERYTHING digital is nothing but a series of ones and zeros in strings of eight digits. For instance, when you type the capital letter A on a computer, the machine reads that A as the binary code 01000001. A capital B is binary code 01000010. So on and so forth, right?
When you think about that fact, that everything you’re looking at on this screen is really a series of numbers, it’s kind of baffling…like we’re in the Matrix or something. Your bank account. Your kid's online grade book. Your social media. That photo you uploaded of the salad you ate last Wednesday. All of it - ones and zeros.
So let’s get nerdy(er)!
So you get that everything digital is just coded language a computer can translate. Ones and zeros. Cool. So how do we protect that information if we want to keep it secure, but we want to send it across the internet? Well…grab your pocket protector.
I’m not going to make this super technical, but there is value in understanding what happens when you secure information via encryption…and it’s pretty cool the way it works.
When you decide to use something that encrypts your data, what happens in a very simplistic form is that data, the ones and zeros, is scrambled. Remember A being 01000001? Well, with it being encrypted, that A might actually be 00001010, as an example.
What next?
This is the cool part, at least to me. So we have this load of code, millions of strands of ones and zeros, and we want to make sure prying eyes don’t see it, and if they do, they can’t make sense of it. It’s time to get our keys ready.
When data is encrypted, keys are generated that allow those with them to decrypt that data and make sense of it. Without the key, all you have is a bunch of arbitrary ones and zeros in binary form. Useless, really.
Now, how these keys are securely shared is the most technical part and isn’t something that I’m going to get too deep into here. Just know that there is a super cool way that involves some serious geekery/magic/math to make it work that keeps these keys safe from prying eyes. There are several ways to do this, but you really don’t need to know much about it. Again, I’m nerdy, and I don’t totally understand it. (Truth be told: I don’t think I could do it justice trying to explain it here…or anywhere. It’s complex.)
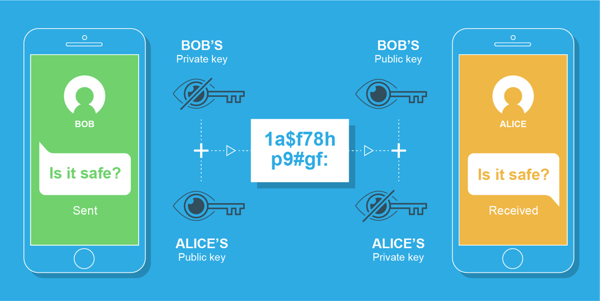
Ok. Zeros and ones. Eights are there somehow. Keys. So what?
This is where it all comes together. Undoubtedly, you’ve seen things like 128-bit encryption or 256-bit encryption listed on things, right?
First, let’s get this idea out of the way. Generally speaking, because there are other forms of encryption, the higher the number, the stronger the encryption. Right now, the gold standard is 256-bit encryption. What’s more, you always want end-to-end encryption. This means when you send the data, it’s encrypted, AND if it lands on a server and sits somewhere, it’s encrypted there, too. This is a REALLY good thing.
Let’s marry ourselves to the 256-bit encryption for this example. (By the way, if your data is less than 256-bit encrypted, you may want to consider other options that can provide higher levels of security. Like everything, data thieves are evolving, and sometimes, 128-bit encryption isn’t enough.)
What this means for your data is that to open and understand it, to make it actually data and not just random binary code, without the keys, you would have to guess a 256-character password. This has a probability of 4 billion x itself 8 times. Without the keys, this is virtually impossible. If you had 100,000 supercomputers and each was able to try a million billion keys each second, it would still take trillions of trillions of years to crack.
Get your stuff encrypted!
Regardless of the systems you have in place, from onboarding to client communications to workflows, if your systems aren’t properly secured, ideally with 256-bit end-to-end encryption, you’re leaving yourself, and your clients, super vulnerable. Don’t take this lightly.
One of the easiest ways to make sure this is happening is by using hosted apps in the cloud. With the right vendor, encryption and, therefore security, are automatic. Peace of mind comes from knowing you and your clients are protected the way they should be.
.png?width=150&height=63&name=TWRlogo-regmark_blueblack%20(1).png)
.png)








Do you have questions about this article? Email us and let us know > info@woodard.com
Comments: